In a earlier post I went through installing a single remote desktop session host server. The post can be found here. The screenshots shown below overview the installation of the RDSH role.
As this is a test lab, I will not be installing a Licensing Server.
So, install the RDSH role on both servers and add ‘Domain Users’ to the local ‘Remote Desktop Users’ group.
RDSH Certificates Template
We now need to configure the RDSH servers to use machine certificates obtained from an enterprise CA. All servers involved in the provision of remote applications to connecting clients require machine certificates. Each server will obtain its own machine certificate from an Enterprise CA. This will be used for remote desktop connections. However, I have found that you will need to share a signing certificate amongst both RDSH and RDCB servers (this certificate originated from RDSH1). I will show you how to create a suitable certificate template on the CA which we will use to enrol a needed certificate on each RDSH server.
Now that you have created a new certificate template that will be used by the Remote Desktop servers, you should define revocation information on certificates your CA will publish. This is detailed in an earlier post (See Step 1 Configure Enterprise CA to Support AIA Extension to Support OCSP). This post will also explain the importance of OSCP in overcoming any revocation errors that you might receive when connecting externally.
The next logical step would be to obtain suitable machine certificates for the RDS servers.
Manually Obtain Machine Certificates on Your RDS Servers
Now that the RDS certificate template and the correct revocation settings have been made, you can now obtain the necessary machine certificates. Use the following procedure:
Configuration of Remote Desktop Session Host Configuration and its Certificate (Do this on each RDS server)
To configure a certificate used to digitally sign the RDP file (Do this on both RDSH servers farm members)
I have found that it helps to use the same machine certificate across both RDSH servers and on the RDCB server. You will have to export the certificate with private key (therefore a .pfx file) from RDSH1 to RDSH2 and to RDCB. To export the certificate, just right click on the personal machine certificate in a MMC and select Export. Then import the certificate onto the other machines using a MMC once more. Once the certificate has been exported/imported you can now deal with configuring that certificate to digitally sign the RDP file.
First, configure a certificate used to digitally sign the RDP file by using RemoteApp Manager.
Domain joined clients will automatically have the CA root certificates stored in their trusted root store. They will not need personal machine certificates only the trusted root certificate in order to validate certificates received from the RDSH servers.
Setting Up Authorization
A chain of authorization needs to be set up. The RDSH servers needs to authorize the RDCB and in turn the RDCB will authorize the RDWA server. You must add Web Access and Connection Broker Servers to TS Web Access Group on Session Host Servers (RDSH1 & RDSH2)
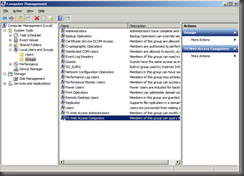
Now on the Connection Broker add the Web Access servers to the TS Web Access group. You can do this through Computer Management like above or you can do it using the RD Connection Manager.


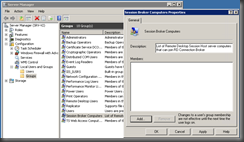
Add Session Hosts to Session Broker Computers Group on Connection Broker
Now we need to add our Session Hosts to a group to give them the ability to use the Connection Broker. Add them to the local group in Computer Management.
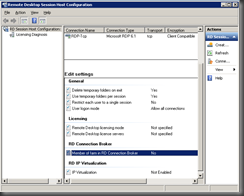
Configure Session Hosts to Use Connection Broker (RD1 & RD2)
Now all of our Session Hosts need to be configured to use the Connection Broker’s services. On each RDSH:


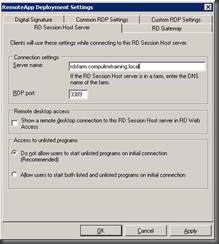
Configure RemoteApp to Connect to RD Server Farm
We need to provide the RD farm address so that clients will connect to it when running RemoteApps. On each Session Host:

Configure Connection Broker for RemoteApp Programs Source
Now it’s time to configure a RemoteApp source for the Connection Broker. On the Connection Broker :


Configure Web Access Servers to Use Connection Broker RemoteApp Source
If you have come this far your doing well! We need to make sure the Web Access Server is configured to use Connection Broker as the source for our RemoteApps. On each Web Access server :

Configuration of NLB
We now need to consider our method of initial load balancing. Remember, clients don’t talk to the RD Connection Broker role service directly; they connect to a farm, which sends this connection to the RD Connection Broker to let it find the right endpoint. So, the farm is connected to first (lets call it the initial connection) and then the connection broker, and then to RD Session Host server in the farm! We will use NLB as our method of load balancing the initial connection to the RDSH farm.
NLB distributes incoming connections evenly across each load-balanced server on the principle that if the incoming requests are evenly distributed, the traffic should be, too. NLB is best for load-balancing servers when the connections are very short, like web servers, or in this case, the initial connection in a farm that is participating in RD Connection Broker load balancing. NLB is more complicated to set up than RR DNS, but it’s capable of detecting when a server is no longer available and will not attempt to send connections to it.
To configure an NLB cluster, you need to complete the following steps.
As this is a test lab, I will not be installing a Licensing Server.
So, install the RDSH role on both servers and add ‘Domain Users’ to the local ‘Remote Desktop Users’ group.
RDSH Certificates Template
We now need to configure the RDSH servers to use machine certificates obtained from an enterprise CA. All servers involved in the provision of remote applications to connecting clients require machine certificates. Each server will obtain its own machine certificate from an Enterprise CA. This will be used for remote desktop connections. However, I have found that you will need to share a signing certificate amongst both RDSH and RDCB servers (this certificate originated from RDSH1). I will show you how to create a suitable certificate template on the CA which we will use to enrol a needed certificate on each RDSH server.
- On the Enterprise CA, under the Certificate Template Node, select Manage and duplicate a Web Server certificate. Select Windows 2008.
- Give the certificate an appropriate name.
- On the Security tab, ensure that all servers involved are placed on the security ACL tab with 'Read' and 'Enrol' permissions.
- On the Request Handling tab, ensure that the Allow Private Key to be Exported is selected
- On the Subject Name tab, ensure the Supply in the Request radio button is selected.
- Select the Certificate Template Node, right click and select New. Locate the duplicated certificate just created and ensure that it is listed in the Certificate Template list.
Now that you have created a new certificate template that will be used by the Remote Desktop servers, you should define revocation information on certificates your CA will publish. This is detailed in an earlier post (See Step 1 Configure Enterprise CA to Support AIA Extension to Support OCSP). This post will also explain the importance of OSCP in overcoming any revocation errors that you might receive when connecting externally.
The next logical step would be to obtain suitable machine certificates for the RDS servers.
Manually Obtain Machine Certificates on Your RDS Servers
Now that the RDS certificate template and the correct revocation settings have been made, you can now obtain the necessary machine certificates. Use the following procedure:
- On your RDS servers, log on as Administrator
- Type MMC in Run
- Select File, Add Remove Snap-in
- Under Available snap-ins, select Certificates and click Add
- Select Computer account and click next
- Select Local computer and click finish and click Ok
- On the Certificates snap-in, select the Personal node, right click and select All Tasks, Request New Certificate
- Click Next on the Before You Begin window and click Next again
- Select the certificate template created above and select the blue hyperlink
- Under the Subject tab type a suitable Common Name. If the certificate is to be used and sent externally (on the Internet) then you should use a public DNS name. Click Add.
- Under Alternative name, select DNS and add names corresponding to both public DNS and any private FQDNs. The DNS name should also include the name of the farm that you intend to use (plan wisely!). At this point, you should add the host record (mapping farm name to an IP address) to your internal DNS server. The IP address used will be the IP used for your NLB cluster (more on this later!)
- Under General tab, write a suitable name and description for the certificate.
- Under Private Key select make Private Key Exportable. You may need to copy the certificate to other servers at some point (that is certificate and private key)
- Click Apply and OK to finish the wizard
- You should repeat this procedure on both RDSH, RDCB servers and for the RDWA server (with suitable external and internal names).
Configuration of Remote Desktop Session Host Configuration and its Certificate (Do this on each RDS server)
- Select Admin Tools, RDS and then open Remote Desktop Session Host Configuration.
- Under Connections select RDP-TCP properties
- On the General tab you will probably find the Certificate is set to Default. Using the select key make sure you define the certificate you installed above.
To configure a certificate used to digitally sign the RDP file (Do this on both RDSH servers farm members)
I have found that it helps to use the same machine certificate across both RDSH servers and on the RDCB server. You will have to export the certificate with private key (therefore a .pfx file) from RDSH1 to RDSH2 and to RDCB. To export the certificate, just right click on the personal machine certificate in a MMC and select Export. Then import the certificate onto the other machines using a MMC once more. Once the certificate has been exported/imported you can now deal with configuring that certificate to digitally sign the RDP file.
First, configure a certificate used to digitally sign the RDP file by using RemoteApp Manager.
- Log on to RDSH1 as Domain\Administrator.
- Click Start, point to Administrative Tools, point to Remote Desktop Services, and then click RemoteApp Manager.
- Under the Overview section, click Change next to Digital Signature Settings.
- Select the Sign with a digital certificate check box.
- Click Change.
- On the Confirm Certificate page, select the appropriate certificate, and then click OK.
- Click OK to close the RemoteApp Deployment Settings dialog box.
Domain joined clients will automatically have the CA root certificates stored in their trusted root store. They will not need personal machine certificates only the trusted root certificate in order to validate certificates received from the RDSH servers.
Configure the RD Connection Broker server (RDCB server)
On a separate member server, install the RD Connection Broker role service. Import the digital certificate used by RDSH server to the Personal certificate store of the computer (remembering to import a PFX file). Then configure the imported certificate used to digitally sign the RDP file.- Open Remote Desktop Connection Manager. To open Remote Desktop Connection Manager, click Start, point to Administrative Tools, point to Remote Desktop Services, and then click Remote Desktop Connection Manager.
- Under the Virtual Desktops: Resources and Configuration heading, click Specify next to Digital Certificate.
- On the Digital Signature tab, select the Sign with a Digital Certificate check box.
- Click Select.
- In the Confirm Certificate dialog box, click the certificate that you want to use for signing the RDP files, and then click OK.
Configure the RD Web Access server (RDWA server)
On a separate member server, install the RD Web Access role service.You will need to obtain a certificate for this server like you obtained a certificate for the RDSH server from the Enterprise CA.Setting Up Authorization
A chain of authorization needs to be set up. The RDSH servers needs to authorize the RDCB and in turn the RDCB will authorize the RDWA server. You must add Web Access and Connection Broker Servers to TS Web Access Group on Session Host Servers (RDSH1 & RDSH2)
- On each of your RD Session Hosts go to Start > Administrative Tools > Computer Management.

- Open Local Users and Groups and select the Groups sub-folder on the left, then double click the “TS Web Access Computers” group in the center.
- Add the names of your RD Web Access and Connection Broker servers.
Now on the Connection Broker add the Web Access servers to the TS Web Access group. You can do this through Computer Management like above or you can do it using the RD Connection Manager.
- Go to Start > Admin Tools > Remote Desktop Services > Remote Desktop Connection Manager.

- On the Actions pane, click Add RD Web Access Server.

- Enter the FQDNs of any RDWA servers
Add Session Hosts to Session Broker Computers Group on Connection Broker
Now we need to add our Session Hosts to a group to give them the ability to use the Connection Broker. Add them to the local group in Computer Management.

- Add each RDSH server to the list
Configure Session Hosts to Use Connection Broker (RD1 & RD2)
Now all of our Session Hosts need to be configured to use the Connection Broker’s services. On each RDSH:
- Select Admin Tools, Remote Desktop Service, Remote Desktop Session Host Configuration.

- Double-click ‘Member of Farm in RD Connection Broker’ which is under ‘RD Connection Broker’

- Under the RD Connection Broker tab click the Change Settings button.

- In the resulting RD Connection Broker Settings window, you specify how this RD Session Host server will interact with RD Connection Broker—that is, what the relationship is. Choose Farm Member and then enter the RD Connection Broker server FQDN and the farm name in the input boxes (see above). You should use the FQDN rather than flat NetBIOS name. This name should be one of the subject names used in the certificate created.
- Click OK and you will be back on the RD Connection Broker Properties tab. The check box next to Participate in Connection Broker Load Balancing is selected by default. Leave it selected.
- The weight describes its capacity relative to the other RD Session Host servers in the farm. Although all RD Session Host servers should be configured identically, not all will necessarily have the same amount of
memory or the same number of processor cores. For example, if a server is only 75% as powerful as other servers in the farm, then you can reduce its weight to allow it only 75% as many connections as the other servers. The default value is 100.
- Also by default, the redirection method—how a client connects to the RD Session Host server once RD Connection Broker decides which server should accommodate the connection—is set to Use IP Address Redirection. If the initial load balancer allows clients to connect directly to RD Session Host servers in the farm, keep this default
setting. Unless you have a good reason, you should leave Use IP Address Redirection.
- In the bottom section of this page, select the IP address that will be used for reconnections to this server. NOTE If you have more than one network adapter that you want to use, you can choose them all by checking the box next to each network adapter.
- Perform this process for each member of the farm, taking care to use the same farm name and the same redirection method on all farm members.
Configure RemoteApp to Connect to RD Server Farm
We need to provide the RD farm address so that clients will connect to it when running RemoteApps. On each Session Host:
- Select Start, Admin Tools, Remote Desktop Services and RemoteApp Manager

- Next to RD Session Host Server Settings click Change.

- In the RD Session Host Server tab type the FQDN of the farm then click OK.
Configure Connection Broker for RemoteApp Programs Source
Now it’s time to configure a RemoteApp source for the Connection Broker. On the Connection Broker :
- Select Start Admin Tools, Remote Desktop Services, Remote Desktop Connection Manager.

- Click RemoteApp Sources in the left hand tree, then choose Add RemoteApp Source in the right Actions pane.

- Type the DNS name for the RD server farm then click Add.
Configure Web Access Servers to Use Connection Broker RemoteApp Source
If you have come this far your doing well! We need to make sure the Web Access Server is configured to use Connection Broker as the source for our RemoteApps. On each Web Access server :
- Select Start, Admin Tools, Remote Deskt0p Services, Remote Desktop Web Access Configuration.

- Supply Domain Admin credentials and sign-in.

- Click the Configuration tab heading. Then for “Select the source to use:” choose “An RD Connection Broker server”. Then type in the Connection Broker server name in the “Source name:” field. Click OK. Remember, the RD Connection Broker server has been added to the TS Web Access Computers group on each farm member (RDSH1 and RDSH2).Also we have added the RD Web Access computer account to the TS Web Access Computers group on the RD Connection Broker.
Configuration of NLB
We now need to consider our method of initial load balancing. Remember, clients don’t talk to the RD Connection Broker role service directly; they connect to a farm, which sends this connection to the RD Connection Broker to let it find the right endpoint. So, the farm is connected to first (lets call it the initial connection) and then the connection broker, and then to RD Session Host server in the farm! We will use NLB as our method of load balancing the initial connection to the RDSH farm.
NLB distributes incoming connections evenly across each load-balanced server on the principle that if the incoming requests are evenly distributed, the traffic should be, too. NLB is best for load-balancing servers when the connections are very short, like web servers, or in this case, the initial connection in a farm that is participating in RD Connection Broker load balancing. NLB is more complicated to set up than RR DNS, but it’s capable of detecting when a server is no longer available and will not attempt to send connections to it.
To configure an NLB cluster, you need to complete the following steps.
- If you have a network adapter dedicated to NLB, you need to configure it with static IP and subnet mask
- Install the NLB Manager on a host node or other management machine. To do
this, open Server Manager and select the Features section. Click Add Features, select the check box next to Network Load Balancing, and click Install. - Configure the NLB cluster.
- Open NLB Manager on one of the farm members from Start, All Programs, Administrative Tools, Network Load Balancing Manager or by typing nlbmgr in the Run text box on the Start menu. Right-click Network Load Balancing Clusters and choose New Cluster.
- In the Host input box, enter the name of one of the NLB hosts (one of the RD Session Host server farm members) and click Connect. All available network adapters on that server show up in the lower pane. Select the NLB network adapter and click Next (I am using only a single adapter on each RDSH machine)
- The IP address and subnet mask assigned to the network adapter will show up in the next window. The priority number is a unique number that differentiates the servers. Accept the default value. If you need to make any changes to the address, click Edit and make your changes. Leave the Initial Host State as Started, and click Next.
- On the next screen, click Add and add a unique IP address and subnet mask that will be shared by all cluster members, and then click OK. When users request access to the farm, they will be sent to this address instead of a specific RD Session Host server. This is the ‘Cluster Address’
- On the Cluster Parameters page, accept the defaults, including Unicast for the Cluster Operation Mode setting, and click Next. All cluster host adapters must use the same operation mode or NLB will not function.
- On the New Cluster: Port Rules page, you need to make a few changes to the default settings. Click Edit, and then change the starting and ending port range to 3389 (in both the To and From fields) because you will be using this cluster to load-balance RDP traffic only. In the Protocols section, select TCP. In the Filtering Mode section, choose
Multiple Hosts to allow multiple hosts to handle traffic for this port rule. For Affinity, you have three choices; none, single and network. Choose Affinity: None so that incoming connections can be sent to any member of the farm. (There’s no reason to set affinity when the connections are being redirected, and doing so could make your load-balancing efforts useless by sending repeated connection requests to the same server.)
4. Add a DNS entry mapping the farm name to the cluster IP address.



My internal domain name is westwood.com but another company owns the domain on the outside. I created a SAN cert for exchange using the netbios name and modified the EWS URL to match the netbios name. This resolved my cert mismatch problem. Can I do the same for the RDS Farm name? I was thinking about getting a cert and using rdweb.westwoodgroup.com (outside for Web) and SAN netbios names in the cert for the farm and inside servers. All would be consistent w/all 3 internal servers.
ReplyDeleterdweb.westwoodgroup.com (common name)
Netbios name (Farm Name)
netbios name (inside server)
netbios name (inside server)
netbios name (inside server)
Would this resolve the cert mismatch errors? In the RD session Host server name properties on the remote app server i would just set the Farm name to the netbios name and not the FQDN name and use the cert for signing also. Worked for Exchange 2010 with users connecting internally to the CAS :) even though Microsoft doesn’t like using netbios! Too bad we don’t own westwood.com or our internal name was westwood.local....The cert would come from a third party digicert. Could i use one single SAN cert for all servers?
Would it be wise to install the NLB manager on the RDCB server?
This sounds ok. As long as the Internet DNS name and internal names are on the cert you should be good. I think using the same cert on each RDSH server should not give you any problems also (infact I have used the same certificate for signing and I have received no errors). You should also be able to manage the NLB cluster from either a node in the cluster or outside. Let me know how you get on. You dont need me to tell you, but it would help if you were using .local inside!
ReplyDeleteOne of the many joys of cunsulting. You walking into a network that wasnt set up right! We are looking to move to Colo in a month with a point to point dedicated 1gigabit line between both sites. I was going to run remote app over the line to a RDH Farm for 80 users. I am looking to get approval this week for the project. I want to dot allmy i's and cross all my t's. Your website is excellant! I installed remote desktop gateway and RDH server with published apps 8 months ago and it has been working great. Now its time to move to the Farm topology. I will keep you updated on the progress. Thanks for your quick reply!
ReplyDeleteGood luck with the approval!
ReplyDeleteI have been approved! I will order the Point to Point line to the colo and all the network equipment. I have before May 13th to get it all done. Not a log of time but it should do! Digicert has a cool tool so I can create the SAN cert on the server instead of using certreq.exe with an ini file. I will update with my progress.
ReplyDeleteNice one...lot of work in a short space of time. Good luck
ReplyDeleteHey Andrew, running into an issue I'm hoping you can help me out with. I have a RD farm with a WA, RW, CB and 2 x SH's. How can I create the CSR's for creating my cert with digicert? Since IIS is not installed, I have no way to do it. How do I overcome this?
ReplyDeleteSorry to sound like an idiot..but dont you order the certs using digicert's online CSR tool? I am sorry to ask but why the reliance on IIS? SAN certs can be ordered aswell. I have relied upon using an Enterprise PKI solution having put the CA on a DC. Domain members (all Win 7 clients) will have a root certificate just by being in the same forest. This is all they need. Your Remote Desktop servers can obtain needed certificates from your own CA. The only problem here is if you try to offer hosted applications to non-domain clients. They of course will not have the needed trusted root cert. To be honest, my experience in purchaing certs from Digicert is limited. If you can provide a homegrown solution you would be better off!
ReplyDeleteAndrew
I understand about having my own CA but went the route of using digicerts online csr tool. I have everything up and running with 3 nodes in the farm along with the session broker. Took a few tweaks with windows xp3 to get SSO working correctly. Ciso doesnt play well with IPv6 which caused my nlb cluster to fail with dcom errors. Running the MS hotfix to completly disable Ipv6 allowed my three nodes to converge. Ipv6 doesnt work well with cisco switches. Do i need to add a second nic to manage the devices? Since everything is sent to the broker i get redirected to the same server unless i reboot that server I can access the other one to make changes. Kind of annoying!!
ReplyDeleteI am the guy working on the point to point l2 gigabit line that posted the above comment. I saw someone else asked you a question about iis. Just want to make sure you knew who was posting. My last post was in April so it's been a while!
ReplyDeleteFirstly, I'm sorry for the delay in writing. WRT the second nic..I havent found the need to have a second NIC (but I would need to test it). And yes it is confusing knowing who is posting what considering you are called anonymous. !!
ReplyDeleteI was thinking about having the second nick and setting it up like you would for heartbeats in a cluster. No default gateway and no registering in DNS. I would hit it just by IP to log into each rdsh server so I could manage the remote app section and I wouldnt get redirected to the session broker to a single rdsh everytime I try to log into each rdsh by DNS name
ReplyDeleteI set up another interface in the same subnet on the nlb farm BUT it still redirects me to the broker when trying to access each nlb member individually. I would like to be able to manage the server individually so i can add more remote apps or edit user profiles. I either have to turn off redirection to the broker or hit each server with a different user name so its distributed to the other servers. I guess the only way wuold be to put the second nic on another subnet but i still figure the broker will give problems.....
ReplyDeleteI have followed all of these steps and when I open an app from the web access portion it has a window appear that says a website wants to run a RemoteApp program. Make sure that you trust the publisher before you connect. Once i hit connect there it brings up another window that says "the identity of the remote computer cannot be verified. Once i hit yes there it want me to enter credentials again. What can i do to fix this issue. i have 2 Sh that are part of a farm, 1 CB, and 1 Web Access server. I am running an Enterprise CA that issue the certs for these servers accept for the web access server.
ReplyDeleteWhy does the web access server not have a certificate from the enterprise CA?
ReplyDeletethe web access is using our .org wildcard cert and the other servers are .local
ReplyDeletecan you import the certificate being used by the session host server into the web access server?
ReplyDeletehi, thanks for posting! ive searched a lot for this info, and this is a very good explanation, so thans.
ReplyDeletethanks so much... you save my days... :D
ReplyDeleteHello andrew!
ReplyDeleteGreat documentation here!
Mabey you can help me out here if you like.
I have installed 1 session broker and 2 session hosts.
Remote app login portal on session broker and it wil read out the applications on the other servers.
The session broker server i installed the certificate succesfully.
No security issues at all. But when I start an app I get a security issue. When i look on the host session servers it says: there are no certificates on the host server for remote desktop sessions installed. I installed the cetificate through mmc (personal/certificates). I also cant select a certificate. it is self-signed. The remote-app on the host server is signed successfully with the certificate. But the RDP-Tcp not.
Thanks in advance!
Steph from holland
I have a quick question. First you tell us in #15 "You should repeat this procedure on both RDSH, RDCB servers and for the RDWA server (with suitable external and internal names)."
ReplyDeleteThen you tell us "I have found that it helps to use the same machine certificate across both RDSH servers and on the RDCB server. You will have to export the certificate with private key (therefore a .pfx file) from RDSH1 to RDSH2 and to RDCB."
Which one? Do we only need to manually use the template we created on the CA once and then export/import on all the other servers? Or do we have to use the CA template and manually create the certificate on every server?
Thanks in advance!
Tom